Email has been the most anticipated way of communication among professionals and organizations. As it has been in usage all across the world, therefore its diversity can’t be ignored. Despite its popularity, Email security concerns have consistently persisted. Emails sent from the original senders are decrypted by scammers without the knowledge of the receivers.
However, as technology advances, security issues have been dealt with through various authentication techniques and software. For prevention purposes, three email authentication methods including SPF, DKIM, and DMARC have made their mark.
Purpose of Email Authentication
Email authentication is mandatory for Email address owners to control their incoming mail efficiently. All the steps taken to secure email addresses until now have one main purpose. And it is to secure all the confidential data of both the senders and receivers.
By far email authentication is done by setting rules by the domain owner. These rules help determine if the address is legitimate. Once the email is received, the email receiver cross-checks if the email is according to the preset rules. The email receiver has the option to flag emails coming from the spammer.
Understanding SPF
Sender Policy Framework (SPF) is a protocol that helps identify the authorization of the email source. It sets up the process to identify the authorized email sources by their IP addresses. As a result, it reduces spam and phishing from DNS spoofing domains.
It adds a TXT record to the DNS settings. TXT records make it clear which servers are authorized to send emails. After receiving the email, the recipient server checks the sender’s SPF record. It confirms if the domain, that is sending messages is allowed to send mail or not.
Understanding DKIM
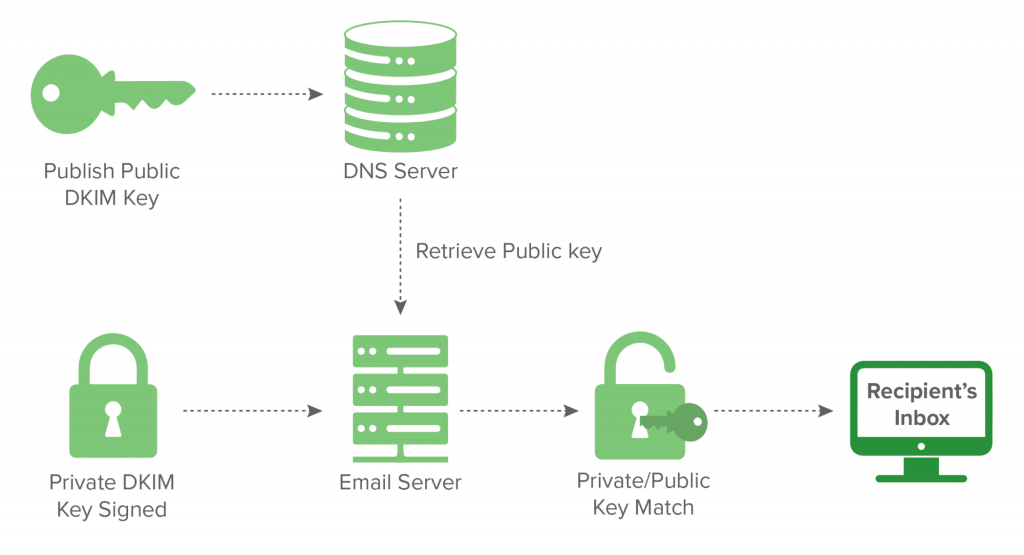
DKIM stands for DomainKeys Identified Mail. It is the second email authentication protocol that helps verify the authentication of email text’s integrity. It doesn’t check the source from where the email is coming from. Rather, it uses digital signatures to verify the authenticity of the message sent by the receiver.
DKIM is programmed to add a digital signature to the header of the email. Only the sending source knows this private key. The address receiving the email gets a public key. The receiver checks the DKIM signature from this public key and decrypts the signature. It is then used to verify the authenticity of the context of the mail.
Understanding DMARC
Domain-Based Message Authentication, Reporting, and Conformance (DMARC) protocol implements rules and policies regarding what would happen to unauthorized emails. It can be used by those Email senders who use SPF and DKIM protocols. DMARC compliance helps recipients avoid unauthorized emails by implementing secure email policies.
Like SPF, it also adds a TXT record to the DNS setting of a domain. As a result, it specifies the way to handle failed SPF and DKIM checks. After receiving the email, the receiver’s server checks if the email is declared authorized by DKIM and SPF. If it is unauthorized, email is dealt with according to the DMARC record policies of the receiver’s server.
How SPF, DKIM, and DMARC work together
The foundation of this three-part email authentication is formed by SPF. SPF, DIM, and DMARC work on effectively securing different aspects of emails. The combined work of all three protocols maximizes the outcome and effectiveness. SPF checker works at the level of email servers. It defines the use of DNS, but it has nothing to do with the email message and the authentication of the domain.
For this purpose, DKIM and DMARC are used. To ensure the authenticity of the source from where the email is coming from, DKIM uses digital signatures. These digital signatures act as a key to confirm the identification of the source. DKIM record stores these keys. Then comes the DMARC protocol which is dependent on both the SPF and DKIM. With DMARC, email receivers get to know what to do with spam mail.
Setting up DMARC, DKIM, and SPF for a domain
Settling these on the servers is not quite easy. Here’s a quick overview. For detailed procedures, you must visit the protocols websites accordingly.
The first step is to set these up in the DNS settings. There are two ways to do this.
- Contact the DNS service provider to set these up in the DNS settings.
- Get a tool from a web hosting platform to upload and edit DNS records.
To set up SPF: Add a TXT record with authorized IP address and domain in DNS settings.
To set up DKIM: prepare a key for both the sender and receiver address. Add it to the domain’s DNS setting.
To run DMARC at the end, specify the required policies for the unauthorized mails and add them to the DNS server.
The Impact on Email Security
For organizations that have earned a reputation in the market, a lot of emails have to be sent daily. And when sitting among the competitors, organizations need to keep their data protected.
According to stats, In 2022, the daily volume of spam emails exceeded 162 billion! This is why an organization is obliged to follow all the mandatory steps to keep its communication platforms secure.
This mandatory email security requirements are achievable through PowerDMARC’s robust SPF, DKIM, and DMARC solutions. It is as important for a business to grow as the investment to start the business. Some organizations are often subjected to show compliance with data protection requirements. Failure to do so can result in serious actions.
Summing up
In today’s technologically advanced era, from communication to transactions, everything is predominantly digital. To keep the data private and secure, every digital platform must enhance the security protocols.
Among all the platforms, the security of official platforms like emails must continuously improve the security protocols. This is achieved by the combination of security protocols SPF, DKIM, and DMARC. This proactive combination ensures the security of emails at each stage of their transmission.